Today, business is conducted primarily with a digital-first mandate, with users expecting safe, secure, and seamless interactions across channels. Ensuring a document’s integrity and the security of the digital information exchanged is paramount for any organization, especially those operating in highly regulated industries. Ever wonder how a digital signature works to keep your organizational, customer, and constituent data safe? Here's a quick overview of the steps that are performed each time a digital signature is applied to a document.
Certificate Assignment
When a user subscribes to a digital signature, they are assigned a digital certificate containing their public information and a unique pair of public/private keys.
Signature Creation
- A standard mathematical function summarizes the contents of the document into a string of characters with a defined length.
- The character string is then encrypted with the unique private key assigned to the signer, whose access can be protected by different methods, such as a password or multi-factor authentication (MFA).
- The encrypted chain, certificate, and signer’s public key are added to the document in the form of a digital signature. This digital signature also includes other unique identifying elements such as proof of revocation verification that ensures the user’s certificate has not been revoked, and a time token certifying when the data was accessed.
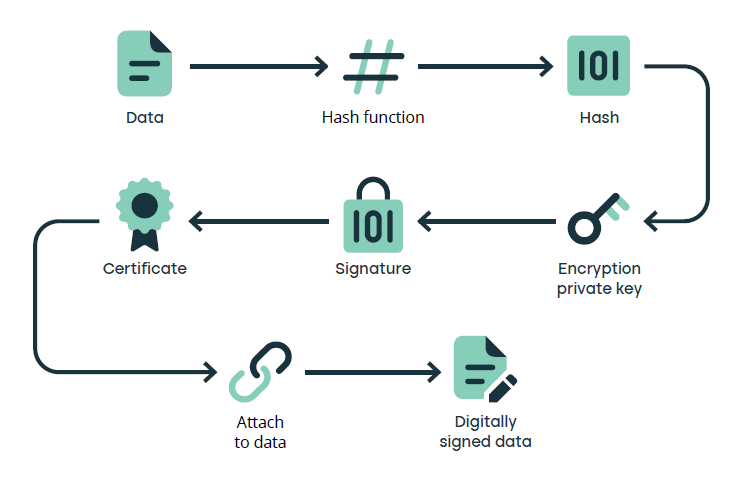
Signature Verification
- When the document is then re-opened with a digital signature compliant PDF reader, its contents are again summarized by the same mathematical function into a string of characters with a defined length.
- The encrypted string included in the digital signature is then decrypted using the individual’s public key in order to recover the original value created during the signature stage.
- If the two strings are identical, it is ascertained that the document has not been modified and all other elements of the digital signature are valid. It can be successfully linked to the identity specified in the certificate and the individual’s set of private/public keys. The document’s integrity is thus validated, and the security of the transaction assured.

